INTRODUCTION
In the 1990s, one of the biggest threats was "dialers"—malicious trojans that disguised themselves as innocent MP3 files and could significantly increase your phone bill if not detected in time. At the same time, however, another insidious type of attack appeared on the horizon—phishing. Unlike dialers, which disappeared with the advancement of technology, phishing has not only maintained its relevance but has also significantly evolved. With the advent of technologies like artificial intelligence, phishing attacks have become even more sophisticated and dangerous.
Phishing was first recorded in 1996, and even decades later, companies still struggle to create effective defenses against this threat. Despite the advancement of cybersecurity systems, phishing remains one of the most common tools in the arsenal of cybercriminals. According to recent data, over 80% of companies worldwide experienced phishing attacks just last year. This further confirms that phishing is not just a temporary problem but a global threat to businesses.
Although phishing often targets individuals, it can be particularly dangerous in a corporate environment. Just one weak link can become the gateway to a serious threat to the entire organization. In the past, phishing primarily used simple emails to steal passwords or financial information. But today, attack methods have become much more complex—they include not only emails but also fake websites, fraudulent text messages, and even phone calls. For example, "spear-phishing" attacks, which target key company employees, use personalized messages that are difficult to distinguish from genuine ones. This makes combating phishing an especially challenging task, even for large enterprises with robust security systems.
Today, we will examine how large companies can effectively deal with this "plague"—phishing—and reliably protect their business from this persistent threat.
What is Phishing?
Phishing is a form of cyberattack in which attackers send fraudulent messages, pretending to be legitimate organizations, to trick people into revealing confidential information.
This type of fraud could simply be called "fishing," but early hackers liked to alter the spelling of words to make them more original or unusual. An example of this approach is also the term "phreaking," which was used to describe phone hacking.
Phishing gained popularity in the early 2000s with the rapid rise of email and social networks. To this day, it remains one of the most common tactics of social engineering. The problem with phishing is that it cannot be prevented solely by technical solutions—it largely relies on the human factor.
Anyone or any company would like to delegate their cybersecurity problems to a newly installed tool and continue enjoying streaming music, watching cat videos, and executing instant stock trades. Unfortunately, there is no ready-made solution for them—or for us—and fortunately for cybercriminals.
Why Does Phishing Work?
Have you ever wondered why phishing emails often contain many errors and poor grammar? This is done intentionally, as such an approach allows attackers to easily filter out the least attentive people—the ones who are more likely to become victims of the attack. Don’t worry, regular hackers know how to use spell check. But today, the situation is even more complicated—in 2024, the "Nigerian prince" might use artificial intelligence to create even more convincing and sophisticated fraudulent messages.
It's no surprise that the European Council considers social engineering one of the biggest threats in the digital space, noting that 82% of data breaches are related to the human factor. Phishing plays on our emotional reactions. You download an attached file or enter your details, trusting the sender, thinking it's a charitable actor and not a criminal who is exploiting your curiosity, greed, or compliance for their own gain.
What Can Phishing Look Like?
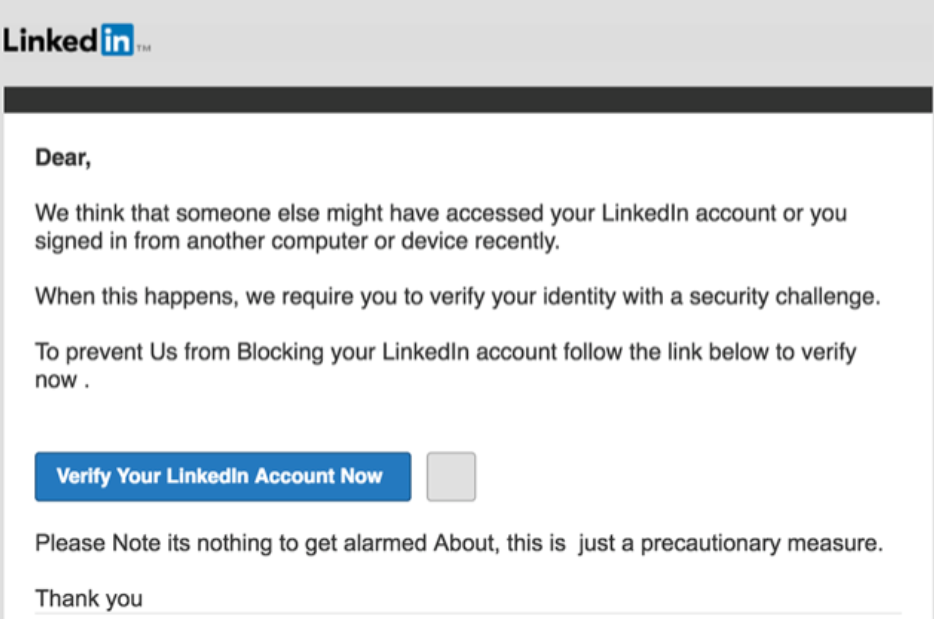
Imagine you're an ordinary person named Sarah, who receives an email from what appears to be "Amazon Customer Service." The subject line reads, "Your Order Has Been Canceled – Action Required." The email explains that there was an issue processing your latest purchase and that, unless you update your payment details within 24 hours, your account will be suspended.
The email looks convincing: it has the Amazon logo, a professional layout, and even a realistic order number. In a rush to avoid any disruption to your service, you click the link, which takes you to a page that looks identical to Amazon’s official site. Without thinking twice, you enter your login details and payment information, unaware that you’ve just handed over your credentials to cybercriminals.
This type of phishing, where attackers impersonate well-known brands to trick users into providing sensitive information, is highly effective because it preys on our trust in established companies and our fear of account issues.
To avoid such situations, it is essential to continuously train employees to recognize phishing threats. People are the first and most important line of defense in a corporate security system, as even the best technical solutions cannot prevent an attack if an employee unknowingly gives attackers access to internal systems. Therefore, investing in employee training and conducting cybersecurity hygiene training is one of the most effective ways to protect a business from sophisticated phishing attacks.
Let's take a closer look at the types of phishing that can threaten your organization.
Types of Phishing Attacks Targeting Enterprises
The risk of phishing attacks is real and significant. According to the FBI (IC3), nearly 300,000 phishing attacks were recorded in 2023, making them the most common type of fraud. Business Email Compromise (BEC) attacks, which are often linked to phishing, caused approximately $3 billion in losses.
A well-known example involves Google and Meta (formerly Facebook), which fell victim to fraud involving $100 million through fake invoices sent to their accounting departments. The employees likely lacked sufficient training to recognize such attacks.
Here are the main types of phishing attacks targeting enterprises:
Spear Phishing
This is one of the most dangerous and common types of phishing attacks on enterprises. Attackers specifically craft their attacks for certain individuals or groups of employees within a company, using detailed information about them. They may impersonate emails from executives, colleagues, or partners to trick the victim into providing confidential data or downloading malware. This type of attack is particularly often directed at top managers and executives who have access to financial information or critical company data.
Example: An attacker could send a personalized email to the head of finance, requesting an urgent money transfer for an important partner. The email might look completely legitimate and come from the "address" of the company’s CEO.
Business Email Compromise (BEC)
A targeted phishing attack that focuses on manipulating business employees to gain access to corporate financial resources or confidential information. Attackers may impersonate company executives, partners, or suppliers. BEC attacks are often used to facilitate financial transfers or obtain critical corporate information.
Example: A fake request for a large money transfer from the "CEO" to the company's accountant, who is urged to complete the transfer to the attackers' account immediately.
Clone Phishing
In this type of attack, cybercriminals create exact copies of corporate websites or popular services used by companies to collect employees' credentials or passwords. Employees may receive links to these fake sites through fraudulent emails or messages. They then enter their logins and passwords, giving the attackers direct access to corporate systems.
Example: An employee receives an email that appears to be from the company's IT department, asking them to log into the company portal using a provided link. The link leads to a fake page where the employee unknowingly provides their credentials to attackers.
Phishing via Phone Calls (Vishing)
Vishing (short for "voice phishing") involves using phone calls to extract confidential information from company employees. Attackers may impersonate technical support representatives or partners to gain access to corporate resources or convince the victim to hand over sensitive data.
Example: An employee receives a call supposedly from the IT department, informing them that to resolve a security issue with the corporate system, they need to provide access to their computer or other confidential information.
Phishing via SMS (Smishing)
Smishing is phishing conducted through text messages, where attackers try to convince company employees to click on malicious links or provide access to internal systems. These attacks can also be targeted at executives or critical personnel.
Example: An employee receives an urgent text message from a supposed bank or payment service requesting them to click a link and verify account details, which leads to a phishing page.
Supply Chain Phishing
Phishing attacks targeting a company’s suppliers or contractors who may have access to internal corporate systems or data. Attackers exploit these weak links to infiltrate the company by compromising suppliers the organization works with.
Example: A fake email from a partner or supplier containing a malicious file, which, when opened, infects the company’s internal network.
Phishing via Social Media
Cybercriminals create fake profiles or accounts on social media to gather information about a company's employees or launch attacks on corporate resources. The goal of such attacks is to gain employees’ trust or create fake accounts impersonating real people to send malicious links or files.
Example: An employee receives a connection request on LinkedIn from someone pretending to be a business partner. After building trust, the attacker sends a message containing a malicious link disguised as a business proposal.
How to Protect Your Business: Expert Recommendations
Implement Regular Phishing Attack Simulations
Phishing attacks remain one of the most common cyber threats, targeting the human factor—the weakest link in any security system. Regular phishing simulations allow organizations not only to test employee awareness but also to identify potential vulnerabilities before attackers can exploit them.
How we do it:
Threat vector analysis: Our cybersecurity specialists first assess the potential risks to your company. Taking into account the specifics of your business, we determine which phishing scenarios are most relevant.
Real attack simulation: We create personalized phishing campaigns that mimic real threats. Emails may be disguised as messages from executives, partners, or official institutions. Our approach allows you to test employees' ability to recognize suspicious emails and avoid falling into the trap.
Monitoring and analysis: After launching the simulation, we analyze employee behavior: who opened the email, who clicked the phishing link, or entered their credentials. This allows us to evaluate the overall level of awareness and vulnerability within the company.
Feedback and training: After the simulation, each employee receives feedback. Those who made mistakes undergo additional training to enhance their cybersecurity awareness. Our specialists conduct training sessions based on identified gaps, helping to strengthen cybersecurity across the organization.
Expert tip from ESKA:
"The best results come from phishing simulations conducted without prior warning, using the latest social engineering tactics. This provides a real picture of employees' readiness for phishing attacks. We recommend conducting these simulations quarterly, with result analysis for further improvement of security policies." - notes Maksym Sypko, CISO of ESKA.
Employee Training
Regardless of the complexity of technical measures, a company’s security often depends on the awareness and skills of its employees. Poorly trained employees can become an entry point for attackers, making them a key target in social engineering-based attacks.
Key elements of employee training:
Threat recognition: We regularly conduct training where employees learn to recognize signs of phishing attacks, such as unexpected password change requests, suspicious attachments, or requests for confidential information. These sessions are based on real case studies and the latest social engineering techniques.
Password hygiene: Using strong passwords and changing them regularly is a critical security element. We recommend implementing password manager policies and training employees on how to create unique, complex passwords.
Multi-factor authentication (MFA): Implementing MFA at every level of access makes it much harder for unauthorized users to enter systems, even if a password is compromised.
Expert tip from ESKA:
"Regular cybersecurity training should be interactive and personalized for each role within the organization. For example, training for administrative staff differs from that for technical personnel, as their roles are associated with different risks." - notes Maksym Sypko, CISO of ESKA.
3. Investments in Email Filtering Systems and Multi-Factor Authentication (MFA)
In addition to employee training, technical measures play a critical role in minimizing risks. Email filtering systems and the implementation of multi-factor authentication (MFA) significantly enhance an organization's security posture.
Email filtering systems: Many phishing attacks start with an email. Investing in filtering systems allows for automatic blocking of malicious emails, spam, suspicious attachments, and links. Modern solutions utilizing artificial intelligence can detect and analyze suspicious patterns, even if the email appears legitimate.
Integration with SIEM systems: We recommend integrating filtering systems with SIEM (Security Information and Event Management) systems to improve monitoring of suspicious activity and ensure rapid response to potential threats.
Multi-factor authentication (MFA): MFA significantly improves security by adding an extra layer of protection when accessing systems. This is an effective method against password theft attacks. The combination of passwords with one-time codes or biometric data makes it nearly impossible for attackers to gain access.
Innovative authentication methods: We recommend implementing not only traditional SMS-based MFA but also modern approaches such as hardware keys (FIDO), fingerprint authentication, or mobile apps, which minimize the risk of data theft.
Expert tip from ESKA:
"Protection should not be limited to using passwords alone. Combined with MFA, we recommend employing adaptive authentication policies based on behavioral analysis. This enables the system to track suspicious activity and automatically block logins that deviate from a user's usual behavior." - notes Maksym Sypko, CISO of ESKA.
Cybersecurity is not just a task for the IT department; it's the responsibility of every employee. Are you sure your people, processes, and systems are securely protected from cyberattacks? ESKA can help you find out. Engage us as your cybersecurity expert to identify and eliminate weak spots in your IT infrastructure. Schedule a consultation with our specialists today and take the first step toward strengthening your business security: Consult with an ESKA expert.

We all understand that protecting a business from cyber threats in 2024 requires a multi-layered approach, which includes regular phishing attack simulations, employee training, and investments in cutting-edge technical solutions. A combination of these measures helps reduce the risk of system compromise, protect confidential data, and minimize potential financial and reputational damages. By implementing modern cybersecurity strategies, business owners can be confident that their business remains resilient to the most advanced cyber threats.
FAQ
Why are phishing attack simulations important?
Phishing simulations are crucial because they address the human factor in cybersecurity. They go beyond theoretical training, which may not be effective for all employees, by providing practical experience in responding to phishing attempts in a safe and controlled environment. By regularly conducting such simulations, organizations test and improve employees' ability to detect and respond to phishing attacks, creating a continuous learning process. This approach results in a more resilient team capable of recognizing and minimizing potential threats.
Can phishing attack simulations improve enterprise security?
Yes, phishing attack simulations are a proven and cost-effective method for significantly improving enterprise security. They act as a proactive measure to strengthen an organization's first line of defense—its employees. By simulating real phishing scenarios, these exercises enhance employees' ability to detect and respond to such threats, reducing the likelihood of successful cyberattacks. Regular simulations ensure that employees remain aware of the latest phishing techniques and continuously reinforce the importance of cybersecurity. Additionally, insights gained during simulations help improve overall security strategies and protocols.
Should all employees participate in phishing attack simulations?
Absolutely. All employees, regardless of seniority or position, should participate in phishing attack simulations. Cyber threats do not discriminate by role or level, making it essential that everyone in the organization takes part. Each employee is a potential target and could become the entry point for cybercriminals seeking access to the company’s confidential information. Ensuring universal participation in phishing simulations reinforces collective responsibility for cybersecurity and increases awareness of cyber threats across the organization. Such a comprehensive approach ensures that all employees, from newcomers to executives, are equally prepared to recognize and counter phishing attacks, turning every potential entry point into a defensive stronghold.
How often should phishing attack simulations be conducted?
Phishing attack simulations should be conducted regularly, with a frequency that balances effectiveness and training fatigue. The recommended approach is to conduct these simulations quarterly. This frequency allows employees to stay up to date with new phishing techniques while avoiding training becoming too predictable or routine. It is important to note that this recommendation may not fit all organizations. Some companies may require more frequent training, depending on various factors such as compliance requirements, current security levels, industry, and risk appetite. Advanced simulation tools using AI can optimize the frequency, offering risk-based phishing approaches where higher-risk employees receive training more frequently.
How do phishing simulations differ from real phishing attacks?
Phishing simulations are designed to closely mimic real phishing attacks in appearance and technique, making them highly effective training tools. The main difference lies in the consequences. Falling for a real phishing attack can result in serious data breaches or financial losses, often with long-lasting consequences. However, in a simulated environment, those who fall for the attack do not suffer any real harm. Instead, they receive immediate feedback and learning opportunities.
What are the alternatives to phishing simulations?
Alternatives to phishing simulations include interactive cybersecurity workshops, security awareness training, and regular cybersecurity newsletters to keep employees informed about current threats.





Comentarios